Contents
What is SSO?
Single Sign-On (SSO) technologies allow organizations to invest in SaaS applications while retaining central control of passwords, access to control lists and multi-factor authentication schemas. Just as importantly, SSO allows users to access all of their applications with a single set of credentials. Keep in mind, even if an SSO is enabled, the user will still need to have an account created in Betterworks.
Why Use SSO with Betterworks?
There are many compelling reasons to use Single Sign-On with Betterworks and the other cloud applications your business uses:
-
Improved employee efficiency
-
Do you have trouble remembering many different sets of credentials? Do complex password policies frustrate you? Many users experience these frustrations. By implementing SSO, users are able to access all of their corporate resources with a single set of credentials.
-
-
Enhanced password security
-
When people have to remember many passwords, they tend to either write them down or repeat the same passwords for all of their applications. Using the same password to access many different sites means the password is only secure as the least secure site in the group.
-
-
Reduced risk
-
With SSO implementations, the SaaS application doesn’t handle authentication tasks, like password resets, and passwords are not stored within the SaaS application. Because these are managed centrally, vectors for hacking and phishing attacks are minimized. All user authentication information is passed between servers using 256-bit SSL encryption.
-
-
Centralized control
-
Using SSO solutions, corporations can centrally manage access to all of their corporate applications, control password complexity, implement multi-factor authentication schemas, leverage on the fly provisioning and keep user identity information in sync from a central user store.
-
All SSO implementations require the following:
-
An Identity Provider (IdP): an entity that manages user authentication
-
A Service Provider (SP): the application or resource a user wants to log in to
-
A secure connection and communication protocol between the IdP and the SP
The (2) most common standardized communication protocols are:
-
Security Assertion Markup Language (SAML)
-
OAuth (Open Authorization)
For information on either setup, see the following articles:
Using SAML 2.0
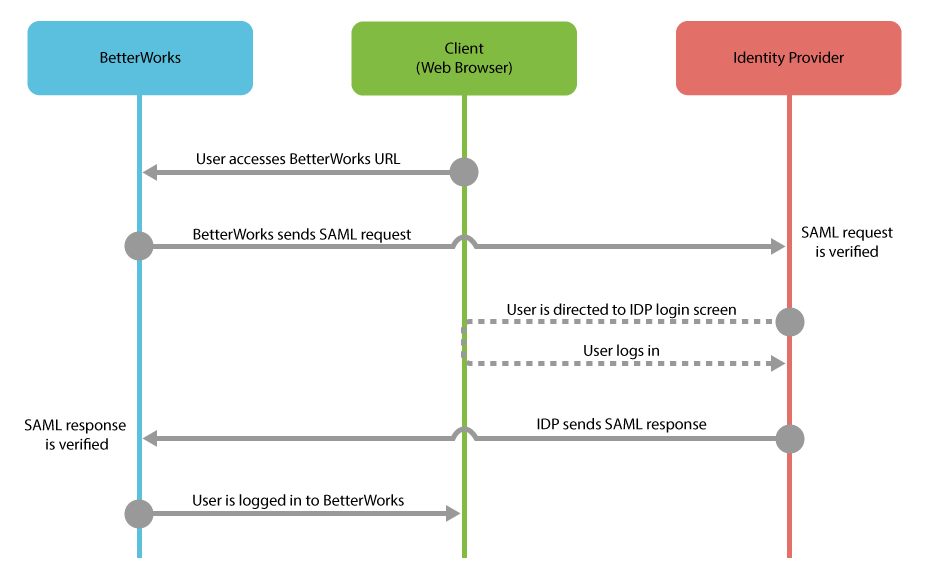
Betterworks communicates with your organization’s IdP to get the information it needs to authenticate users and allow them access into Betterworks, whether they’re connecting from a web browser or using mobile apps.
There are (2) ways that employees might connect with Betterworks when using SSO:
1. Initiating the session from the identity provider (IdP initiated)
2. From a Betterworks login screen (SP initiated)
Using Google OAuth
This is another example of an SP Initiated login flow:
-
The user goes to app.betterworks.com
-
Or eu.betterworks.com if the organization's instance is on our EU datacenter
-
-
They enter their email address
-
Click "Log In"
-
Based on the domain at the end of their email address, the user is redirected to their organization’s SSO page
-
They enter their credentials
-
The password is verified within the SSO’s website while the email address is sent to Betterworks for authentication
-
If the email address sent to Betterworks matches what we have on file for the user, authentication is successful and the user gains access
-
If the email address doesn't match, authentication fails and the user is denied access
-
Mobile Apps with SSO
The Betterworks mobile app has an embedded browser.
For an SSO enabled Betterworks account, users will be able to perform SP initiated login flows. Currently, the Betterworks mobile app is not compatible with IdP initiated login flows.
Also, in configurations where the IdP is not web facing, it may be necessary to either move the IdP login service to the DMZ, or ensure mobile devices are within the Virtual Private Network (VPN) so that users are able to reach the IdP's login page.
Please consult your IdP's instructions for details on how to make the login flow compatible with mobile devices.
